Cycle stealing (grid/distributed computing)
Cycle stealing (grid/distributed computing)
Cycle stealing or CPU scavenging is a concept in distributed computing that relates to utilizing networked resources to accomplish a common computational goal. Some computational tasks can easily overwhelm limits of a single dedicated computer, and cycle stealing is a method for providing additional computing horse power to a task.
Banks, insurance companies, hedge funds, and many other businesses use so-called distributed or grid computing for their modeling efforts. Imagine a bank with a portfolio of tens of thousands of stocks, bonds, options, and other instruments. For the bank to manage risk, finance and economic analysts need to run models to try to estimate how their portfolio will react to market and economic changes. Running such models on such portfolios is something that needs much more horse power and data than a single stand-alone computer can handle. Banks and insurance companies often build so-called distributed and/or grid networks.
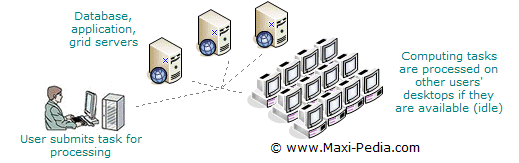
Cycle-stealing is the first step in building distributed networks, and it works in a way that additional resources are connected through the corporate network to the main processing unit.
Where do the other computers and other resources in a grid or distributed computing come from? This can be enlightened by looking at the following example. Let’s start off with a question:
How much do you use your computer?
Some may say, "all the time." Some may say, "less than you think." However, in the perspective of a 24 hour day, most workplace users use their computers for less than 50% of their work day, which roughly equates to 4 hours per day out of a total of 24 hours. This works out to a daily utilization of 17%. This figure may seem low, but it is actually higher than what the latest studies suggest.
Studies show that the average PC user at work utilizes his or her machine at a rate of 13% per day with an average consumption of less than 8%. This consumption figure points to the amount of load placed on the PC’s processor (you can view this by right-clicking on the Windows Taskbar and selecting Task Manager and clicking the Performance tab). A large number of users use their machines only for email, web traffic, and word/excel processing. With the ever-increasing speed and capabilities of today’s desktop hardware, this leaves IT professionals with a disproportionate share of unused capacity.
This leads us into grid computing in a shared environment. If the average user uses his or her PC for 4 hours per day, then there are 16 hours left in the day for this machine to still have value. What about your lunch hour, what is your PC doing then? How many meetings do you have a day? What about when you go home at night? What if we could harness these unused clock cycles for the common good? This is also called cycle-stealing.
What is cycle stealing?
Cycle-stealing is a grid-related policy-driven service which transparently recruits unused resources from the network for the grid or distributed computing system based on system criteria. When these grid criteria determine that you are not currently using your PC, your computer starts processing grid tasks. In order to prevent using the computer by the grid at the same time when the user uses it and slowing him down, the cycle-stealing mechanism is intelligent enough to distinguish between a trip to the water cooler and your trip home based on these policies.
How does cycle stealing relate to grid computing?
The term "grid computing" relates to joining geographically and politically independent distributed computing environments, but many business people use the term "grid" for any complex cluster of computational resources. For the simplicity of our explanation, we will use the term "grid" in the narrower sense now as well, that is in the meaning of distributed computing to be compatible with the language business people use.
Grid computing virtualizes the processing resources of multiple grid engines. A grid engine is just another name for your computer; it is the object of the cycle-stealing method. Grid engines are hardware resources with a small grid application running in the background. These grid engines establish themselves as available to a grid server. A grid server is a central management unit which authenticates the grid engines and distributes work.
When you have a running grid, next you have to supply work for it to process. This is done through client applications. Users run grid-enabled applications from their desktop which submit jobs to the grid server. Authenticated grid engines then pull this job’s tasks. A grid engine pulls work from the grid server until it is disrupted. If the engine does not successfully return the completed work, the grid server offers the work to another grid engine.
A collection of networked grid engines that work on cycle stealing basis with one or more grid server is what business people often call a grid network.
How large a grid can be?
There is probably no limit to how many engines you can have in a grid. Depending on the application, banks and insurance companies often run grids with 100 - 200 grid engines (dedicated machines) for their modeling. Companies can have hundreds of cycle-stealing engines in their grids.
How fast can a grid be?
It is not unusual to work with a grid that runs at 500 gigaflops or more. A gigaflop is a measure of one billion floating point operations (instructions) per second.
I am a power user who needs a lot of performance, will my PC appear sluggish?
No. The idea of grid cycle-stealing is that the engine is only used when no one is using the host computer. The engine waits a given period of time and determines that you are not currently running an intensive job before it volunteers for the grid.
What about grid computing security?
The grid acts only as a service on your local machine. Engines volunteer for the grid, there is no outside intervention to force your PC to participate in the grid.
Local security is addressed by user privileges. Jobs run on the grid engines as guest users, so they have no rights to user information on the machine.
Server security is addressed by user authentication and encryption. Only those users setup for access to the server are able to gain access. It is also possible to encrypt all engine-server communications.
Data security is addressed through the actual data being passed between the grid server and its engines. Each task submitted to a grid engine is only a small unit of work and each grid engine only witnesses a small percentage of the total execution.
Can I ever notice the grid on my PC?
No. The grid service runs in the background. Users are not be prompted with informational or error messages. Also, the grid engine only requires 15 seconds or so to return the PC for local use, so by the time a user presses CTRL-ALT-DELETE and login, the grid engine execution should have halted.
Does grid leave anything behind on my machine? Does grid fill my hard drive?
No. The grid has the ability to synchronize each engine with whatever files it needs to execute its jobs. These files are stored in a temporary directory. When jobs are completed the output is immediately returned to the submitter’s machine before another set of work is pulled from the grid server. Whenever the engine removes itself from the grid, all temporary storage is deleted.
What applications can be used on the Grid?
Applications to be used on a grid must be grid-enabled to be able to take advantage of grid computing. Software must be designed to work with the grid, either through software drivers or scripts.
It is easy, just include the code provided below into your HTML code.
 Delicious
Delicious Digg
Digg StumbleUpon
StumbleUpon Furl
Furl Facebook
Facebook Google
Google Yahoo
Yahoo